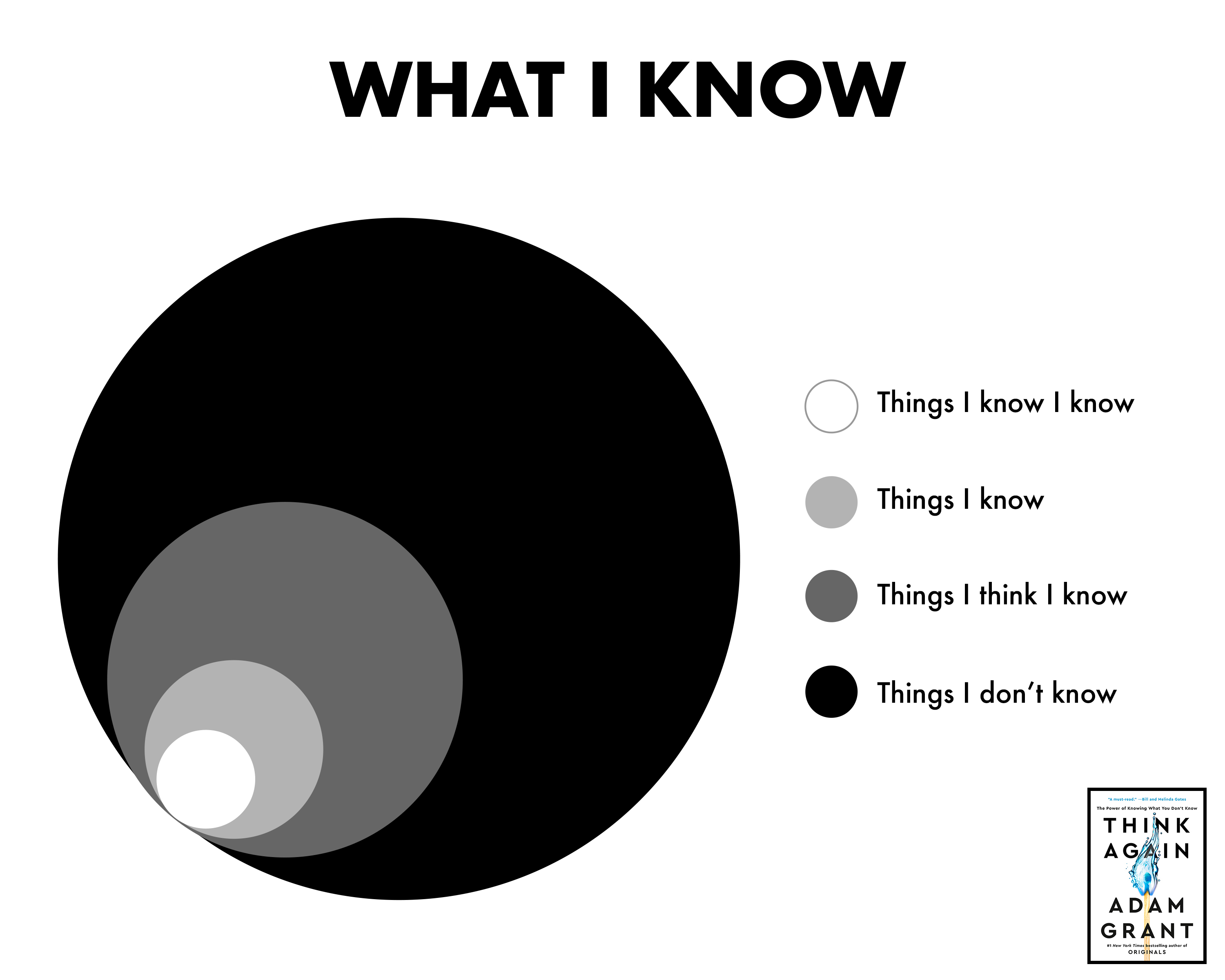
In this article, we will delve into what the thinjen leak is, how it happened, its implications, and what individuals and organizations can do to protect themselves in the face of such cybersecurity threats.
Thinjen Leak: What We Know And What We Don'T
In this article, we will delve into what the thinjen leak is, how it happened, its implications, and what individuals and organizations can do to...