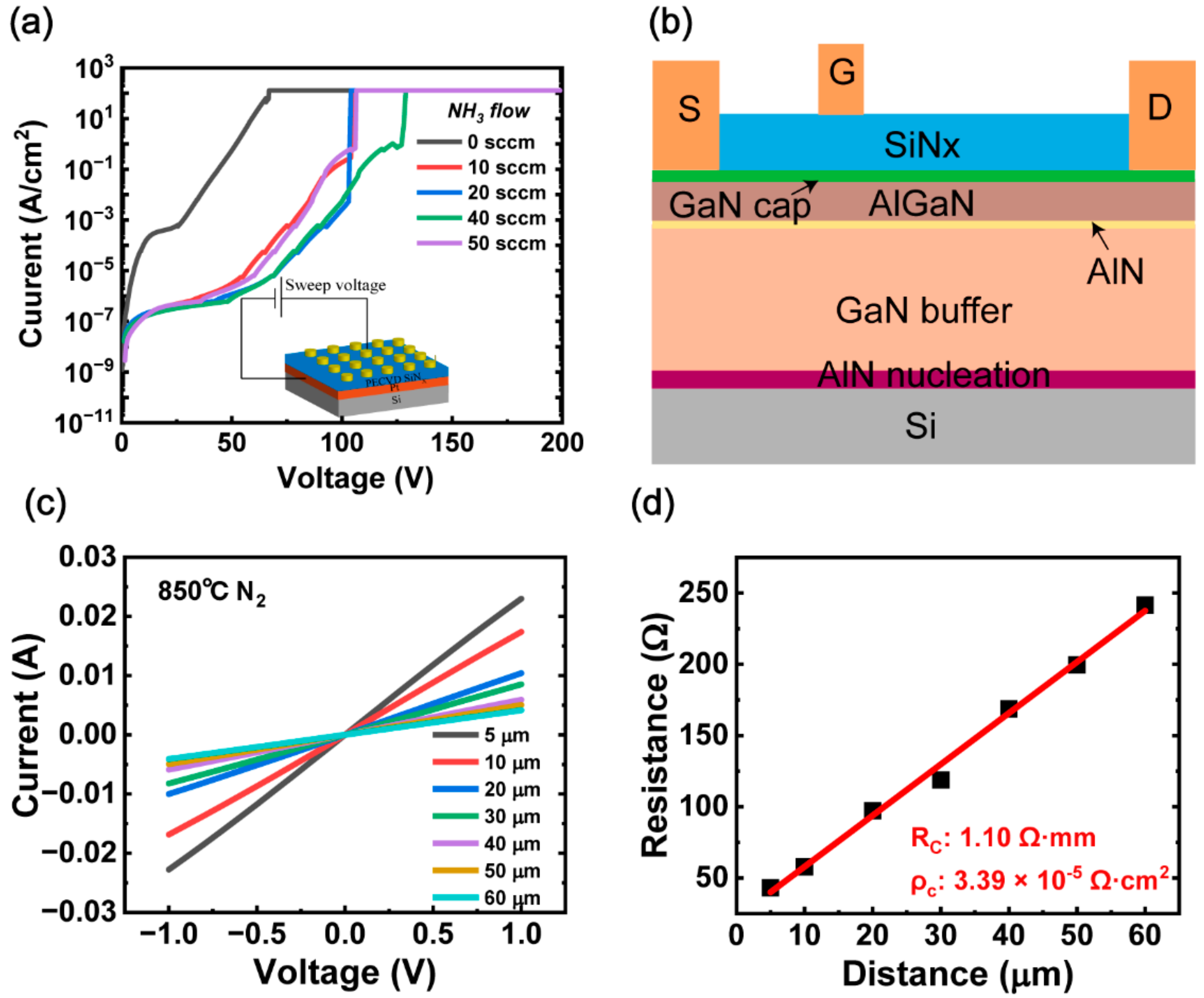
A single memory leak could enable attackers to infiltrate the entire corporate network, leading to potentially devastating consequences, like data theft or ransomware attacks, as blatantly.
Thinjen Leak: A Complete Breakdown
A single memory leak could enable attackers to infiltrate the entire corporate network, leading to potentially devastating consequences, like data theft or ransomware attacks, as...